Technology-oriented company that is nearby customers
- Daou Office, a speedy groupware

- Double-Take

(Real-Time Data Protection & Automatic Fail Over Solution)
A. Perfect data protection with real-time data backup
It protects data safely by performing real-time data replication during online operation for all kinds of application data.
B. Construction of high availability computing environment
It provides a perfect high-availability computing operation environment by system dualization.
A. Real-time data protection: Data dualization prevents data loss due to operational storage failures.
B. Minimized downtime: Minimizes service downtime due to server and storage failures.
C. Provision of high availability of services: Increases service availability for 24 hours to prevent business interruption.
D. Disaster recovery: Provides a disaster recovery environment from site disasters such as computer room fire, flooding, and natural disasters.
E. Live server migration: Increases business availability by minimizing service downtime when migrating servers or replacing servers.
- Doctor Soft

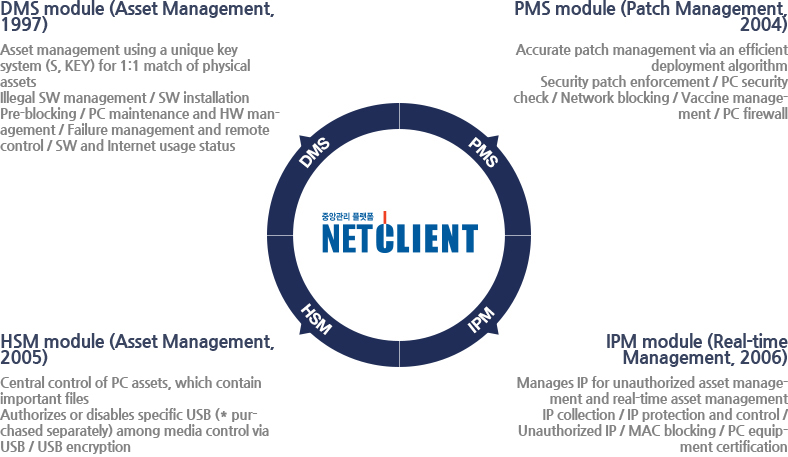
- NetClient
It is the best PC asset management solution for enterprise IT environment.
With proven reliability and technological capability through continuous technological development and securing more than 800 customers, we provide customized solutions with customized function modules in a component-based independent module method.

· Since its launch in 1998, it has been developing its own asset management solutions for the past 10 years (100% self-developed).
· Possession of own development personnel (company attached research institute).
· Product quality certification and patent technology (asset management remote control field).
· Various construction experience - Completed large-scale site and financial projects for the last 3 years100% customized and problem-solving ability through in-house development.

· Developed unique key management technology that can manage one device as one asset, ensuring data reliability by minimizing asset duplication.
· Proprietary key management technology to minimize duplication of assets and manager response method in case of duplication.
· OS reinstallation, prevention of duplication due to ghost, minimization of key change due to redundant key combination of hardware.
· The foundation of an invisible platform is the key to solution success.
· Aggregate PC management function through agent reliability and single agent proven at financial sites.

· Affiliate / large-scale integrated node management and redundancy support.
· Safety - Supports forced installation, anti-agent protection, safe mode support, 64Bit support, Wiindows7 / 8 server support, VMware support.
· Server Scale - The number of PC supports per server (up to 20,000 units), the maximum number of PCs that can be viewed on the administrator's screen (without limitation).
· Reliability - Unique key management technology to minimize duplication of assets and manager response method in case of duplication.
· Supports all networks - Bi-directional support of VPN, private network, router, and NAT IP and provides load balancing technology.
- Wisehub SYSTEMS

The deviation from the path of the information that GRADIUS can block / track / record is deemed leakage.
GRADIUS provides the ability to block and track all leakage routes.
- Shared folder
- E-mail / Webmail
- Network printer
- Web bulletin board
- Messenger
- P2P program
- FTP
- Web hard
- Other unknown network programs
- Local printer
- Portable storage (USB / SD-Card / CF-Memory, among others)
- Floppy diskette
- CD-R / RW, DVD-R / RW
- Bluetooth, Infrared (IrDA)
- Parallel / serial port
- Smartphone / Digital camera (MTP / PTP)
1. Protects important information within the company with real-time spill prevention by keyword / pattern.
- Prevention of real-time leakage by keywords (important keywords in the company such as the core and confidential).
- Protection against real-time leakage by pattern (resident registration number, telephone number, credit card number, and account number, among others).
Satisfies security-related IT compliance (privacy laws, among others) requirements.
- Provides functions such as detecting, tracking, and deleting personal information files on PCs of non-personal information handlers.
- Prevents leakage of personal information files stored on personal PCs and provides encryption function by policy.
3. Strengthens the security awareness of the insiders and disables the will to illegal leakage.
- All information leakage reveals the causal agent.
- Evidence is secured through video playback at the time of information leakage.
4. Real-time disclosure of critical information leaks.
- System halts and manager is dispatched after real-time warning message is issued.
- Indication of stoppage by warning message in case of similar spill.
5. Converts to open system to prevent work efficiency deterioration due to batch function control.
- Opened for use of common devices except for special targets.
- Enables intensive security policy management for key management targets.
6. Achieves transparent information flow through advanced information leakage audit system.
- Transparently manages / watches / tracks / monitor all information flow.
- Achieves establishment and operation of objective and reasonable security policy.
7. Prevention of risk of information leakage against outsourced manpower.
- Blocks all leakage routes when the server is not connected.
- Enables an effective security policy management by special management group.
- NETID

Document management + document security taken care of together at once by ClouDoc
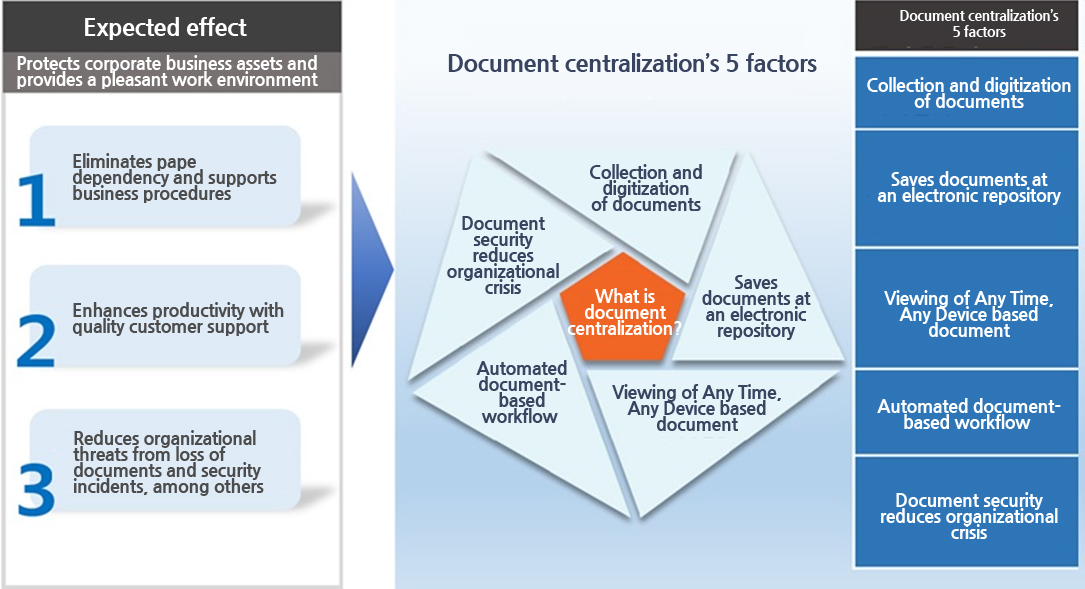
Three main objectives, with five factors of document centralization
- Corporations can systematically manage documents to build a paperless office environment and prevent against the threat of loss and security incidents.
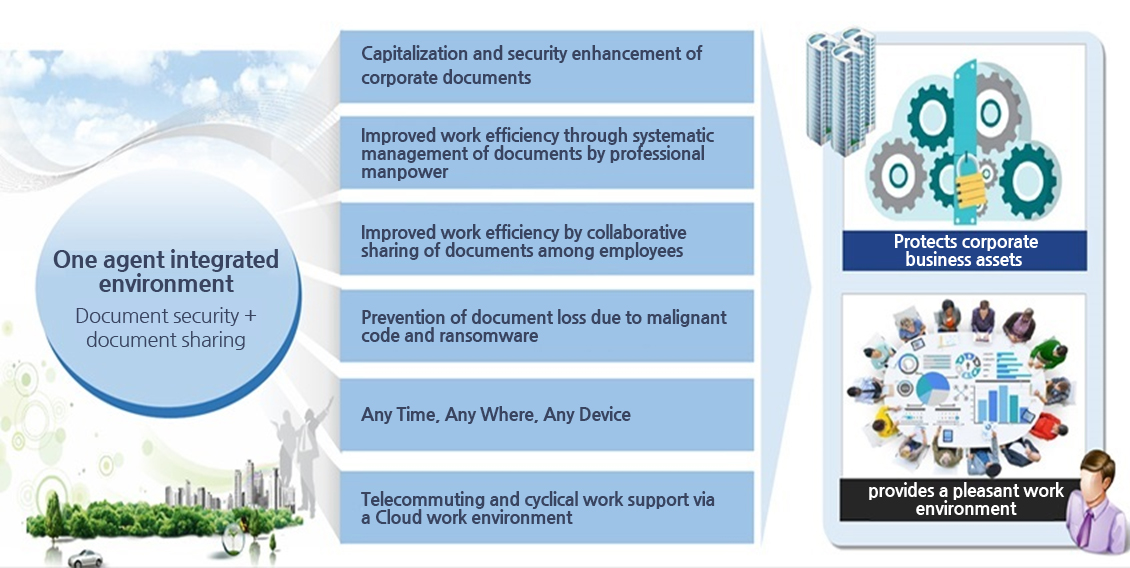
Protects corporate business assets and provides a pleasant work environment
- One agent integrated environment provides a low TCO and convenient maintenance, protects corporate business assets, and provides a pleasant work environment.